Extending Public Key Infrastructure for mobile users via FIDO
The information on this posts is based on the applied research that was performed under the leadership of the U.S. Department of Homeland Security — Science and Technology Directorate on how to leverage the use of derived credentials (NIST 1800–12B[1]) in mobile devices and employing a standards driven authentication protocols.
The key objective of the research was to develop and certify an authenticator that would leverage a strong identity process (Public Key Infrastructure (PKI)) in a mobile authentication (Fast Identity Online (FIDO))process, including the registration and authentication to commercial cloud services, without increasing the technological burden on either party of the transaction and extending current investments into new opportunities.
The approach chosen to meet this challenge was to develop a bridge between current PKI processes and FIDO Alliance protocols; utilizing x.509 certificates. The x.509 certificates provide a digital representation of the original physical credential (Derived Credential) and using such information with the FIDO protocol for authentication to commercial services and other applications.
There are multiple authentication protocols and approaches; FIDO provides an ability to reduce the use of password, avoiding the sharing of secrets and establishing a path to leverage one single credential for authenticating to multiple service providers or relying parties; all in a scalable and interoperable manner with current IdM and security infrastructures.
In this process it is important to understand the definition of a digital identity, for this purpose, we will use the one provided by NIST:
“The unique representation of a subject engaged in an online transaction. A digital identity is always unique in the context of a digital service, but does not necessarily need to uniquely identify the subject in all contexts. In other words, accessing a digital service may not mean that the subject’s real-life identity is known.”[2]
The importance of the description is to understand that such digital identity, must:
Deliver to the service provides the ability to understand and trust the source of the identity (PKI)
To provide an expected level of privacy to the individual (FIDO).
The Challenge and Opportunity — An approach with PKI-FIDO
In the government use case; end users across government agencies want to use their mobile devices to perform their daily functions with the same expectations of frictionless interaction delivered by mobile applications. However, technology managers required the use of PIV smartcards (personal identification and verification) credentials for accessing sensitive government data.
Mobile devices do not provide a simple method to use PIV credentials, without employing external or additional hardware devices, making such deployments technically difficult, operational costly and increase end user complexity.
The use of digital representation of strong vetted credential within the mobile device provides a path to address the shortcoming of the current system.
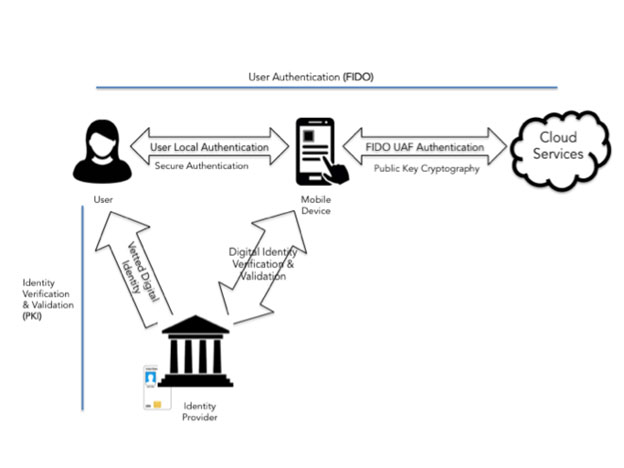
Figure 1 — High-level view of PKI-FIDO Integration
Why FIDO (Fast Identity Online)
As mobile devices and cloud services became ubiquitous, a new level of complexity was added to the identity and authentication sector. In response, the FIDO Alliance[3] developed open and scalable standards that enable simpler and more secure user authentication experiences across many websites and mobile services.
The white paper entitled “FIDO Alliance White Paper: Leveraging FIDO Standards to Extend the PKI Security Model in United States Government Agencies” published by the FIDO Alliance describes the many benefits of FIDO adoption in government or settings where a high level of assurance is required:
“There are compelling reasons for agencies to look to FIDO solutions aside from its security characteristics: its standards-based approach, adoption by key industry players, ease of use, and privacy-respecting architecture and design. FIDO’s lightweight approach to asymmetric public-key cryptography offers agencies a way to extend the security benefits of public-key cryptography to a wider array of applications, domains and devices — especially where traditional PKI has proven difficult or impossible. To be clear, FIDO is not a replacement for PKI but rather complements it, enabling greater number of users and applications to be protected using asymmetric encryption. This is especially important in situations where the alternative has been username and password.”
As a result of changes made by the National Institute of Standards and Technology Digital Identity Guidelines (NIST SP 800–63–3), including the change to separate identity from authentication assurance, the FIDO protocol can now complement PKI in expanding the U.S. Government’s authentication ecosystem as it meets government guidelines for asymmetric, public-key (PK) cryptography for authentication.
FIDO Limitations
One of the limitations of FIDO is the inability to directly integrate with PKI. As a result, government required standard identification credentials are not used in the FIDO authentication process.
The development of a PKI-FIDO Authenticator Integrates Derived Credentials and identity verification into the FIDO authentication process, enabling the use of mobile devices to not only access sensitive data but also the ability to leverage existing credentials for access to a wider range of cloud applications.
How does it work?
As depicted in the image below, the Authenticator consists of a User, a Mobile Device, a Derived Credential, an Identity Provider / Certificate Authority (CA) and a FIDO enabled Relying Party (RL) or Service Provider (SP).
The Mobile Device contains a Derived Credential (represented by the x.509 certificate) , a Service Provider Application, a FIDO Client and the Authenticator.
The Identity Provider / Certificate Authority (CA) provisions the Derived Credential in a secure manner onto the Mobile Device. It also verifies and validates the certificate prior to (a) binding the certificate to the Authenticator and Device with a user’s PIN (Personal Identification Number), (b) registering the user with the Service Provider (Relying Party) and © authenticating the user to the Service Provider (Relying Party) Service.
Once the Credential has been validated, the Authenticator invokes the FIDO process to authenticate seamlessly with the Service Provider.
Identity verification and validation is performed via OCSP (Online Certified Status Protocol) check before the authentication transaction is performed.
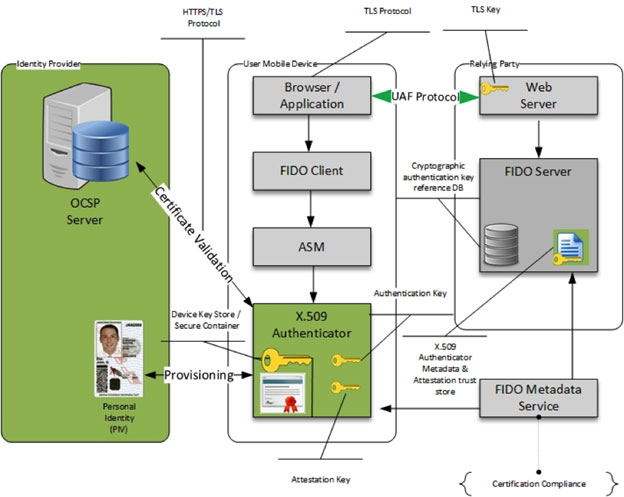

Figure 2 — Architecture of example of PKI-FIDO Authenticator
This adds great utility to the FIDO platform in that it, in effect, PK-enables FIDO authentication in a very simple, private, secure and lightweight manner.
For government applications, this provides the means to utilize FIDO and all of its benefits without the need to create a new FIDO Derived Credential or employ other PK-enablement services.
As a result, the authenticator, can facilitate rapid development and integration of mobile devices into government and private sector systems by providing agencies and commercial relying party applications the ability to achieve the security benefits of strong identity assurance and public key cryptography without the traditional cost and complexity of PKI enabling its applications.
Key Benefits of extending the use of PKI with modern authenticator protocols like FIDO
Credential Management — As the digital credential is rooted on the physical one, any changes on the physical one, will be reflected on the operation of the digital one. This is captured via the validation / verification process — therefore the authentication mechanism integrates into current IDM structures and does not require new processes to be implemented.
User experience — Providing the ability to use a single credential for multiple uses increases the value of the investment made on vetting identities, and FIDO delivers a frictionless User Experience that is not relying on the use of complex password and secrets, but on sensors, biometrics or simple non-sharable secrets.
Assurance — By utilizing a binding method between the digital credential, device and individual — organizations can create a process where it closely resembles as a 2F model, without the additional keys or equipment; a) leveraging a vetted credential that represents the user’s identity and is validated before the authentication process, b) PIN number that is not a shared secret and is only known to the user and lastly, c) possession of the mobile device by the end user.
Access Management — By using the digital credential that is rooted on the physical one, it extends the policies that are being enforced to the mobile environment — for example — while the digital credential enables the employee to use bring your own device to access cloud services that are under the contract of the organization, by the same token, when the credential is de-activate it will restrict access to those services, simplifying the management of the polices and access. Providing a security layer to external services under the control of the organizations.
Cost — A) Due to the elimination of the passwords it will reduce the numbers of password resets and management by the organizations. B) Utilizing a standard protocol that its support is already built into many devices and services lowers the development, deployment and operational cost of the technology. C) Extending investments made with PKI infrastructure to be used in mobile environments.
Interoperability — FIDO provides an interoperable solution that is not reliant on specific mobile devices and is standards driven.
Scalability — The use of two leading standards, and the mobile platform, ensures that developers can focus on the application layer, instead of developing connectors for individual devices, sensors or infrastructure, reducing time to development, reducing deployment and operational cost and complexity.
Summary:
The value of this approach is that is not limited to the government use case, as it can be deployed for any type of strongly vetted digital identities that are represented by an x.509 certificate and are rooted on established and trusted verification and validation process.
Organizations should investigate the use of the digital identities as an extension to current methods and security postures.
They can not only provide financial benefits by extending their current investments into mobile and cloud ecosystems, but also can improve their security posture while extending a pleasant authentication experience to their end users and clients, especially as the new FIDO2 protocols are adopted, extending a password-less experience to the browser with the strength of MFA.
Disclaimer
The underlying applied research and work for this project was performed under the “The Mobile Authentication Interoperability for Digital Certificates (MAIDC)” project that was funded in part by the United States Department of Homeland Security’s Science and Technology Directorate under contract #D15PC00001. The content of this post does not necessarily reflect the position or the policy of the U.S. Government and no official endorsement should be inferred.
Key Terms:
Personal Identity Verification (PIV)
The PIV card was developed to satisfy the requirements of HSPD-12 (Homeland Security Policy Directive), which requires a common identification standard for all Federal employees and contractors and is based on the PKI standard.
A personal identity verification (PIV) card is a United States federal smart card that contains the necessary data for the cardholder to be granted access to Federal facilities and information systems, providing appropriate levels of security for all applicable federal applications.
References:
NIST 1800–12 Draft — Derived Personal Identity Verification (PIV) Credentials
https://www.nccoe.nist.gov/sites/default/files/library/sp1800/derived-piv-nist-sp1800-12-v2.pdf
NIST 800–63 — Digital Identity Guidelines
https://pages.nist.gov/800-63-3/sp800-63b.html
NIST 800–157 — Guidelines for Derived Credentials
https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-157.pdf
FIDO Alliance White Papers
https://fidoalliance.org/wp-content/uploads/FIDO-UAF-and-PKI-in-Asia-White-Paper.pdf
https://fidoalliance.org/wp-content/uploads/FIDO-Deployment-Case-Study-K-FIDO_170905.pdf
Additional Documents
Mobile Authentication Interoperability for Digital Certificates (MAIDC)
https://docs.wixstatic.com/ugd/3bbf1e_102eb762cd8b4227891f55abbb756ab5.pdf
World Economic Forum — Digital Identity — On the Threshold of a Digital Identity Revolution
[1] https://www.nccoe.nist.gov/sites/default/files/library/sp1800/derived-piv-nist-sp1800-12-v2.pdf
[2] NIST 800–63–3
[4] https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-157.pdf



