If you had asked me a few years ago to list the domains of cybersecurity that excite me the most, I certainly would not have listed vulnerability management (VM). One of the most fundamental and important domains, yes. But exciting? No way. Sure, seeing the loooooong list of “critical” security issues after running my first vuln scan or two 20+ years ago was pretty cool…but it quickly lost its luster, and I was glad to move on to other domains.
That’s why I was a bit skeptical when a company approached us about conducting some research related to VM. But they offered data from their platform on several hundred organizations’ vulnerability detection and remediation practices, and I’m a sucker for that kind of analysis. So, we took the project, and three years later, I can honestly say it’s been some of the most exciting and impactful research of my career. I’ll highlight some key lessons in this article.
First off, VM is a hard problem. You probably already know that if you’re reading this article, but let me put some numbers around that statement. There are over 180,000 vulnerabilities on the CVE List as of this writing. 2021 set a record for the most vulns published in a year (nearly 21,000) and 2022 shows no abatement.
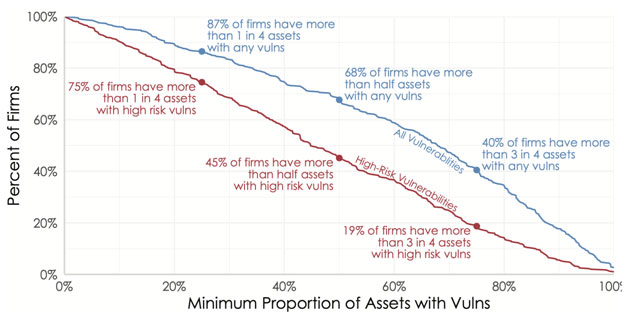
But vulnerabilities published on the CVE List are just an external indicator of the challenges facing VM programs. The real test is how those vulnerabilities affect internal systems, and Figure 1 gives those measures. Over two-thirds of organizations have open vulnerabilities in at least half of their production systems. And about 1-in-5 have high risk exposures (vulns with known exploits) in >75% of their assets!
How are organizations remediating these vulnerabilities? “Struggling” is an appropriate answer, but let’s put another stat on that. Figure 2 plots organizations (blue dots) based on the average number of vulnerabilities detected across all their assets (x-axis) and the average number remediated each month (y-axis). While there’s some variation among firms, the overall trend is remarkably consistent. Organizations typically close about 15% of their open vulnerabilities in any given month, regardless of the size of their IT environment!
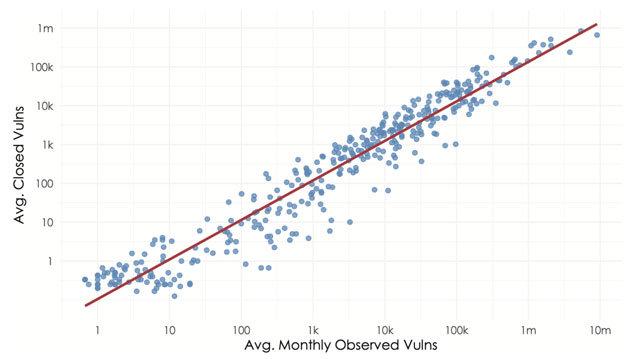

If that seems hopeless and you regret reading this article, give me a moment. The data has signs of hope, and we’re headed there now. We just need a quick detour back to the notion of “high risk” vulnerabilities. It’s critical to establish that not all vulnerabilities represent a real and present danger to your organization. Our analysis shows that less than 10% of published vulnerabilities are actively being attacked and/or have exploit code available to facilitate those attacks. Given the remediation capacity shortage demonstrated in Figure 2, doesn’t it make sense to prioritize exploited vulnerabilities first?
The Cybersecurity and Infrastructure Security Agency (CISA) seems to think so. CISA recently issued Binding Operational Directive 22-01 to reduce risk associated with exploited vulnerabilities. The Directive was accompanied by a catalog of known exploited vulnerabilities maintained by CISA, including mandatory remediation deadlines. I think it’s a smart move in the right direction by CISA, and I have one more chart to prove it.
The analysis behind Figure 3 is similar to that of Figure 2 in that it measures the ratio of open to closed vulnerabilities in organizational environments. But Figure 3 narrows the focus to just vulnerabilities with known exploits. It thus addresses the all-important question “Is it possible to remediate the vulnerabilities that represent the highest risk to my organization?”
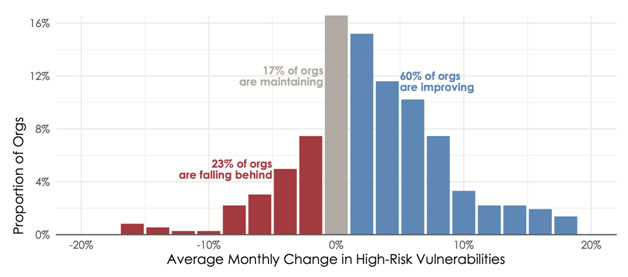

The good news is that Figure 3’s answer is a resounding “Yes!” A full 60% of organizations drove down the number of exploited vulnerabilities, while another 17% maintained pace with new exposures over time. That means over three-quarters of firms are successfully remediating the vulnerabilities that matter most!
And that, my friends, is why I’m so excited to be involved with managing vulnerabilities again. VM programs have long suffered an endless cycle of find-and-fix in a futile effort to keep up. But it doesn’t have to be that way, provided they can effectively prioritize remediation efforts. And this analysis proves that VM teams like yours are successfully doing just that to reduce risk for their organizations. Go get ‘em!



