Whether you are logging into your email, opening a bank account, voting, buying insurance or doing any number of other things, your identity is the critical factor that allows you to act in those instances. It is recognition of this fact that has led to regulations across the world to ensure that positive identity is established before financial services are supplied.
A second factor is that as technology has evolved and become pervasive, the world has digitised, and criminals have also digitised and become more sophisticated. Criminals have discovered that if you can attack/compromise/steal identity, you’ve got the keys to the castle, without the risk of a physical interaction.
We also face the situation of dealing with insider threats of two types. The first is an employee or agent using legitimate privileges to commit a crime or fraud against the organisation. This could be in the form of a payment to a fraudulent supplier account or it could be in the form of claiming commission on a non-existent customer sales transaction as an example. The second type of insider threat is that of an auditor. The power of audit and compliance has grown internationally, due to well publicised senior level compromises of the financial services trust model in some organisations, that ways must be found to do competitive business whilst still keeping compliant and even more importantly, having proof of this.
One could argue that there are only two things that are important in competing today and they are lowering friction and offering trust.
That brings us to the trust model framework for business services.
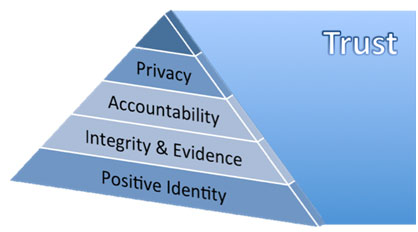
We break down the trust model framework as follows:
- Establish positive identity, be able to prove it and then protect it;
- Protect the integrity of the identity data in the information systems.
- Secure the actions of staff or intermediaries who act with customers on behalf of business, through biometric strong authentication. There has to be governance and technology applied around these processes so representatives can be held accountable for their actions or, alternatively, proved innocent if falsely accused;
- Ensure the customers privacy is protected.
To execute on this stack, there are a number of processes that need to be established and followed.
The process of securing the identity of stakeholders kicks off with a biometric live capture process. This serves to establish positive identity through capturing biometric information at the relevant point of contact wither in an office, through an agent or as self-service. Part of this process is ensuring the right data/biometrics is captured and that it is secured as at capture.
The process of capturing biometric data then triggers a workflow process where things need to be checked and approvals given on what has been captured. This workflow triggers an action – a policy is granted, money is lent, or a database is updated. If someone dies, for example, the relevant database needs to be updated so that a pay-out can be effected to the beneficiary.
In these aforementioned processes, we look at dealing with insider threats first before we deal with anything else. Why insider threats? Because from an attacker’s perspective, a legitimate employee with privileged access to a system or process is the most direct route to achieve the goal of obtaining a stolen identity that can pass scrutiny. If privileged insiders are not open to being bribed with money then coercion can make them do it.
You need to protect the organisation against insider threats. We have found that the best way to do that is to improve the security of the systems by implementing biometric strong authentication. This makes people aware that their fingerprint or face image is at the scene of the crime they have just committed. We also implement digital signatures to seal the evidence of what has happened. This has proven to be highly effective – if you can sort out insiders first they will be more diligent when dealing with customers. This approach also protects innocent stakeholders – if a change is made on a computer system programmatically or through a hack for example, it can be proved that it wasn’t them and that there was foul play, which can be further investigated.
New technologies and service orientated architectures are being brought to bear on the IT environment in all organisations. Concepts such as inter-departmental or inter-organisational federation are becoming a fundamental building block of the immensely sophisticated information systems being deployed.
It is imperative that organisations maintain control of the security of these new structures through a uniform method of identification and strong authentication and the ability to enforce non-repudiation. The approach has to be to abstract the identity and evidence security from the individual business systems and deploy a governed architecture that provides consistent security, standardisation and legal enforceability.
Once this is done, digitising identity leads to further projects where rapid ROI can be achieved such as digitising paper processes and even avoiding having things on a piece of paper at all. Anything where there is paper in dealing with customers, employees and partners is expensive and inefficient. Once the paper is submitted, the data on it needs to be captured, which is expensive and inefficient and where errors come in. You also need to scan and store the paper originals, which is expensive & inefficient.
Paper-based ink signing is no longer an effective tool for customer applications and business document approval in today’s digital environment. Implementing digital signatures services delivers value on many fronts:
- Allows for remote work in a governed, accountable and secure manner
- Increases process efficiency – Increases process efficiency by electronically signing in internal-to-company approval processes & reduce customer frustration when waiting for ink signatures; staff are free to do core business rather than chase paper.
- Cut paper-related costs – printing, couriering, faxing, scanning, searching for paper documents & archiving are all time-consuming and expensive processes. On top of this ink signatures are insecure which can lead to fraud, compliance failure costs, heavy fines & reputation damage.
- Increase security – ensure the digital identities of your transacting parties are verified securely and signed documents are cryptographically locked from unauthorised change; ensure legal certainty using an indisputable evidence trail.
- Eliminate errors and re-work – by putting the approval process into a digital workflow with digital signatures, the signing system can prevent documents from being submitted with missing signatures, initials or incomplete form fields.
- Increase visibility – track the true status of your documents, know with certainty that your documents were indeed received, reviewed and signed by each signatory with the exact date/time each action was performed based on trusted time server.
- Provide a great user experience – make life simpler and save time for your customers, employees & business partners by doing business smartly. Demonstrate your digital security innovativeness and ultimately increasing your brand loyalty. This is especially true where biometrics are combined with digital signatures for customer processes.
Establishing and managing identity is without a doubt the area of the business that leads to the most return for the business in terms of savings, risk reduction, reputation protection, compliance and customer protection.



