Have you ever wondered why technical and security governance is so complicated?
In 1967, a group of practitioners formed an association to ensure centralized governance and auditing of Information Technology. ISACA (Information Systems Audit And Control Association), as we know it today, has had a significant impact in helping organizations globally by forming a common body of knowledge, acceptable auditing practices, and practitioner certifications. When Sarbanes-Oxley came out in 2002 in the United States, ISACA quickly took the lead in helping companies by guiding Information Technology control assessments through its COBIT framework. Later, PCI-DSS, ISO, NIST and many other control frameworks followed.
Today, IT (Information Technology) and cybersecurity governance are very mainstream but complicated by a large and growing body of compliance standards and the desire to automate the software publishing process. Good IT governance has fast become the minimum bar for conducting business in the digital era, with each organization encapsulating their IT practices through Policies, Standards and Guidelines. Many companies have dedicated staff internally for helping with a variety of required audits. Yet, the skills required to transfer the complexity of these requirements into code are now lacking in the governance practice. And guidance driven by practitioners without the requisite set of skills is also causing increased costs with extraordinarily little security return on investment.
Complexity born out of well-intentioned guidance has become the enemy of both speed and security. With hundreds to thousands of control requirements being adopted by companies worldwide, it is near impossible for innovators to leverage mandated guidance to achieve the safety these frameworks once intended to achieve. More importantly, while we have seen significant benefits industry-wide from the rise of governance and compliance frameworks, these same frameworks are mostly not keeping pace with this era of digital innovation. The accessibility of these frameworks once created is now gone. Further, when compliant companies started to encounter publicized breaches, the frameworks lost their credibility.
Somewhere between the year 2005 through 2010 when we were nearing the maturity of IT and Cybersecurity governance frameworks, we took our foot off the pedal and did not codify measurement. New frameworks began to pop up and organizations worldwide started to show how their approach was different and somehow better.
So, what needs to be done?
We as an industry need to dedicate cycles towards achieving the governance north star of continuous and measurable improvement. We need to be more mindful about the controls we choose and why. We need to dedicate time and effort towards mapping controls and attack surface to adversary personas so that we know which controls we rely on to reduce the risks posed by adversaries. We need to dedicate effort towards reducing the exploitability of the environments we support. Control thresholds should be set and leveraged. When controls fail, we need to build a root cause analysis that helps us to understand how a control can be made better and invest where it makes sense. Gone should be the days of literal control framework interpretation. Instead, we need to leverage control frameworks for the codified best practices they provide.
The rise of measurement
After more than five years researching control effectiveness and measurement with other industry practitioners, it is now possible to assert a north star key performance indicator (KPI) for security, called Securability. Securability is calculated as:
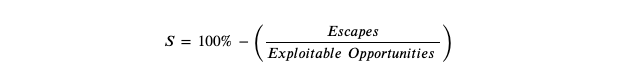
Fashioned after the five 9’s of Availability, this KPI is super simple to work with. Here are some basic principles that were followed in the development and discovery of this metric:
- Makes good look good and bad look bad
- Creates accessibility for both practitioners and the non-expert alike
- Can be leveraged broadly and at the resource level
- Can be rolled up from level to level
- Provides a guide for decisions, trade-offs, and investments
These principles provided a guide that enabled experimentation and lots of use cases to be tested. What we discovered during our collective research is that Securability led to simplification and enabled us to understand which controls work well in our environments and which do not. Further, we have been able to assert whether specified controls lead to adversary resilience in an environment.
How can I apply this measurement?
There are a few methods for using Securability that have been determined through our research. As you might have guessed, most of these methods begin with an inventory of your assets. And while that might be a little daunting, do not be too discouraged because gaps in data simply turn into a question of precision within this KPI.
To enumerate the denominator, called Exploitable Opportunities, you will determine the potential for exploit within your inventory. The denominator should contain both mitigated and unmitigated exploitable opportunities. To answer the question of whether a resource is exploitable, the process should be performed in alignment with an adversary perspective. If you want to jump start this process, you can focus on scan results, where the vulnerability has a known public exploit. This KPI extends far past scan results, but it is a good starting point for those new to measurement.
Escapes come from the result of testing or real-world adversary attacks. If an incident is discovered, then it would be added to the Escapes count. As part of the root cause analysis post-mortem, a practitioner should determine if the Escape exists within known Exploitable Opportunities or whether the reason the incident occurred is due to the gap in inventory information. A proactive approach to creating adversary resilience occurs when Exploitable Opportunities are mitigated prior to release.
Conclusion
In summary, maybe we can live with governance complexity if we were able to simplify it through measurement. Perhaps the world does not necessarily need only one compliance framework where we are able to justify and rationalize our aim at risk management through greater quantification. One thing is certain, the desire for faster innovation requires us to push for measurement to achieve security at scale.






