
Every day we are faced with choices. Do I get up and go to work, or stay in bed? Do I skip lunch and get that report finished, or take a leisurely lunch and let the report sit? Should I buy gas for the car or pay the rent? Should I pay for earthquake or flood insurance or take my chances nothing will happen? Every choice involves some measure of risk. What will happen if I do stay home and not go to work? Lose my job or lose pay for the day? If I don’t pay the rent, will I lose my apartment? How important orimpactful are the choices we make? How do we measure risk? We all make choices, and consequently, we all address the risks incumbent with those choices, whether it’s done consciously or subconsciously.
Is Failure an Option?
Millionaire gone broke Jim Rohn, speaking of risk taking, said “If you are not willing to risk the unusual, you will have to settle for the ordinary”. Jim was born poor, became a millionaire by age 30, and went broke by the age of 33. Jim made choices, risked everything, and came up short. He spent the rest of his life as a great motivational speaker influencing people to risk big and achieve extraordinary success. T.S. Eliot wrote “Only those who will risk going too far can possibly find out how far one can go.” On the other side of the risk spectrum, the fictitious detective Harry Callahan from the Movie Magnum Force said “a man’s got to know his limitations.” But how does he know what those limitations are, and how does he determine when he is approaching those limitations and what will happen if he exceeds those limitations? Ah, assessing and managing risk.
It is one thing to think about choices and risk taking as an individual, but what about risk taking for businesses? Can businesses afford to risk the unusual and potentially lose their business? And since most businesses today use information technology (IT) processing to run the business, how does that technology impact the business? If the business relies totally on IT for product sales and delivery, inventory management, revenue collection, accounting and finance, and customer relationship management, what would happen if IT operations were disrupted, or critical or sensitive data breached or compromised?
In 1971, the first recorded fraud involving the use of computer systems occurred with the Equity Funding Scandal, resulting in the bankruptcy of the company and loss of hundreds of millions of dollars and the conviction of key executives of the company. By 2005, computer hackers had perfected the trade to not only attack and penetrate business computer systems, but also to breach data records and steal the data for subsequent sale on the dark web. Hacking had become a billion-dollar business.
Fast forward to 2022, and computer hackers had evolved into nation-state attackers and organized crime groups successfully phishing company employees, stealing credentials, and planting ransomware to extort millions of dollars in payments in exchange for decryption keys to decrypt critical files that the ransomware had encrypted. By 2022, approximately 77% of all companies attacked by ransomware have succumbed to the attacks, and nearly 40% of the companies have paid the ransoms.
Failure to Comply is Not an Option
In light of the importance of IT to business operations and the massive increase in cyber attacks and data breaches over the past 20 years, the Federal Government and Industry associations across banking, healthcare, and other industries have instituted cybersecurity and risk management regulations, frameworks and standards to force companies to better manage IT risk and risk management within their organizations. Businesses in those industries and those who engage in providing products or services to the Federal government must comply with risk assessment and risk management provisions related to Securities and Exchange Commission (SEC), Federal Financial Information Examination Council (FFIEC), Office of the Comptroller of the Currency (OCC), Health Insurance Portability and Accountability Act (HIPAA), Presidential Directives on Critical Infrastructure Protection, Payment Card Industry Data Security Standards (PCI-DSS), and many other state regulations. Failure to comply with these regulations has resulted in many companies having to pay millions of dollars in fines.
How have companies fared in achieving compliance with the risk management regulations? Not well. Not only have fines been levied upon companies in many industries, but it seems the quality of the risk assessments has been the subject of numerous Federal agencies publishing bulletins disclosing needed improvements in the content and quality of the risk assessments. Fines by OCR for HIPAA compliance violations have now reached the $100 million mark this year. Examples of fines levied upon organizations included the following related to failure to comply with conducting a risk analysis or assessment:
- 2016 – Athens Orthopedic Clinic fined $1.5 million for “longstanding and systemic noncompliance with HIPAA privacy and security rules, including the failure to conduct a risk analysis, implementation of risk management and audit controls, failure to maintain HIPAA policies and procedures, failure to secure business associate agreement with multiple vendors, and failure to provide training to workforce members.”
- 2018 – Anthem Healthcare fined $16 million for “failure to conduct a comprehensive, organization-wide risk analysis to identify potential risks to the confidentiality, integrity, and availability of ePHI.”
- 2020 – CHSPSC LLC (Business Associate) fined $2.3 million for “longstanding and systemic noncompliance with HIPAA security rules, including the failure to conduct a risk analysis and failures to implement information system activity review, security incident procedures, and access controls.”
- 2020 – Primera Blue Cross fined $6.5 million for “systemic noncompliance with the HIPAA rules, including the failure to conduct an enterprise-wide risk assessment and the failure to implement risk management and audit controls.”
- 2020 – USAA Federal Savings Bank fined $85 million by the OCC for “risk management inadequacies.”
- 2020 – Citibank fined $400 million by OCC for “risk management failures.”
- 2021 – Japan’s Financial Services Agency (FSA) fined Ascendo Markets $15,000 because they “had not followed adequate risk management practices and did not have a compliance monitoring program.”
- 2021 – FAFC was fined $500,000 by the SEC for “inadequate cybersecurity risk assessment.”
- 2021 – FICC was fined $8 million by the SEC for “failure to have adequate risk management policies…”
All of the examples stated above involved massive data breaches. They also involved failure in the risk management or risk analysis/assessment processes. There is a difference between the two.
Differences between Risk Management and Risk Assessment
According to the EPA.GOV website, “Risk Management is a distinctly different process from risk assessment. Risk assessment establishes whether a risk is present and, if so, the range or magnitude of that risk. In the risk management process, the results of the risk assessment are integrated with other considerations, such as economic or legal concerns, to reach decisions regarding the need for and practicability of implementing various risk reduction activities. Risk managers also use risk assessment results as a basis for communicating risks to interested parties and the general public.”
So why did all those companies listed above fail in their risk processes? Let’s start by looking at risk. So, from the National Institute of Science and Technology (NIST) Special Publication (SP) 800-30 definition, “risk is a function of the likelihood of a given threat-source’s exercising a particular potential vulnerability and the resulting impact of that adverse event on the organization.”
What does a success risk management process look like?
A successful risk management process requires:
- A structured methodology based on good practices and a desire to seek continuous improvement.
- Senior management defined risk appetite, risk tolerance and risk strategy that aligns to the enterprise business strategy and goals
- A strong risk governance process to monitor risk management progress and compliance with policy inclusive of key risk indicators (KRI) and key performance indicators (KPI).
- Risk practitioners need to review the current risk management practices of the organization in order to perform the tasks of risk identification, assessment, response and monitoring, and reporting.
Details of the enforcement agencies actions related to fines listed above regarding failure to have adequate risk management processes or policies indicated that there was not senior management “buy-in” or “tone at the top” direction for risk policy development and enforcement. Without a formal risk management process and program, risk assessments are most likely to be ineffective or not be viewed as important for business decision-making.
What does a successful risk assessment process look like?
Simply stated, we want to assess the risk to assets in their use to accomplishing an organization’s business goals. From an IT standpoint, that would be called IT Risk. So how do we start with an assessment of IT Risk? There are four phases:
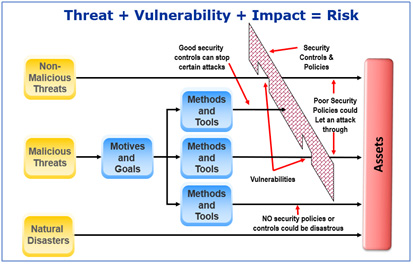
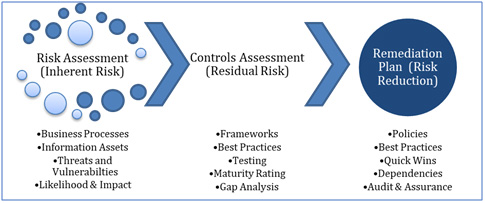
Identification – We need a list of assets used in the business, and then determine the threats, vulnerabilities, threat actors, threat vectors and types of events and timing that impact those assets. Then we determine the likelihood and impact of the risk occurring, and the result is called Inherent Risk.
Assessment – Next we assess and validate the controls currently in place that reduce the likelihood and impact of the identified risks, and any remaining risk called Residual Risk. We look at Senior management risk appetite and tolerance levels to determine if the residual risk exceeds the appetite and tolerance thresholds. If so, then a decision has to be made as to disposition of the residual risk.
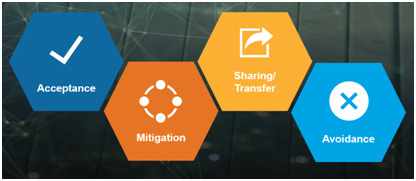 Risk Response & Mitigation – There are four options to address the residual risk. We can accept the risk, avoid the risk, share or transfer the risk, or mitigate the risk.
Risk Response & Mitigation – There are four options to address the residual risk. We can accept the risk, avoid the risk, share or transfer the risk, or mitigate the risk.
The business/application owner owns this decision, in conjunction with Senior Management’s directive. Cost/benefit analysis or Return on Investment (ROI) calculations should be performed to help guide decision making as to the right risk response. Clearly, if a risk response costs more that the risk occurrence impact or the benefit of the control, this is the wrong choice. Once the remediation solutions are identified and prioritized, “quick wins” can be identified that are low-cost and easy to apply.
 Risk and Control Monitoring and Reporting – When risk assessments are ongoing, a risk register is key to monitoring and managing identified risks, and mitigation actions. The risk register also serves as a historical record of open and closed risk items. Reports can be generated from the risk register and KRIs and KPIs generated out of the register for tracking remediation progress.
Risk and Control Monitoring and Reporting – When risk assessments are ongoing, a risk register is key to monitoring and managing identified risks, and mitigation actions. The risk register also serves as a historical record of open and closed risk items. Reports can be generated from the risk register and KRIs and KPIs generated out of the register for tracking remediation progress.
That is what a good process looks like – based on the standard NIST SP 800-30 risk framework.
So why do risk assessments fail?
-
- If we look back at the list of fines above, we see that many of the organizations tried to perform risk assessments; others did not. Of those that did, their organization still experienced a data breach. What happened? The organization failed to adequately assess the risks involved with the underlying application or data. They may have tried to “boil the ocean” in attempting to identify and assess risk, but those efforts were either misaligned or misdirected. One solution to laser-focusing on risk is to take the approach that data breaches happen to critical data. All data is accessed by applications. Why not start the risk identification process by:
- Identifying all critical data
- Identifying the applications that process that data
- Determine the threats, threat actors, threat vectors, impact and likelihood
- Build out use case scenarios for all possible or likely risk scenarios
Prioritize by highest risks, and focus on those risks for response/mitigation

- Risk assessment training played a big part in risk assessment failure.
- Failure of the risk management team to understand the business and the risk assessment process resulted in inadequate planning and execution of the risk assessment/analysis process.
- Failure to read, understand and incorporate regulatory requirements regarding risk assessments for the particular industries also contributed to risk failure and fines.
- If we look back at the list of fines above, we see that many of the organizations tried to perform risk assessments; others did not. Of those that did, their organization still experienced a data breach. What happened? The organization failed to adequately assess the risks involved with the underlying application or data. They may have tried to “boil the ocean” in attempting to identify and assess risk, but those efforts were either misaligned or misdirected. One solution to laser-focusing on risk is to take the approach that data breaches happen to critical data. All data is accessed by applications. Why not start the risk identification process by:
-
- Lack of cyber risk awareness also played a big part in compliance failure as organizations were not prepared for the latest risk vectors and threat actors “in the wild” that might affect their organization, and ultimately did lead to a data breach.
- Senior management did not provide effective direction and policy to drive effective risk assessments.
- There was no apparent risk governance process in many of the cited compliance failures.
- Adequate funding may have played a part in the inadequacy of the risk assessment process at the cited organizations. Inadequate funding leads to training lapse and spotty, inconsistent risk assessment coverage.
What should an organization do?
It is clear that organizations must:
-
-
- Take a more serious and concerted effort to build, execute and maintain a strong risk management program and process. After all, cyber attacks and cyber risks are increasing. They are not going away.
- Communicate the risk program to all personnel, especially business and data owners.
- Promote a risk-aware culture within the organization.
- Fund the risk assessment process and control mitigation solutions.
- Hire competent risk practitioners.
- Pay attention to regulatory compliance mandates that require at least annual risk assessments
- Obtain better threat intelligence information and tools
- Implement a strong risk governance process, including the use of an automated electronic governance, risk and compliance (eGRC) tool.
-






